This article explains how Google Authenticator app works. Two factor authentication (abbreviated as 2FA) is all the rage these days, and for all the good reasons. It prevents unauthorized access to your online accounts by providing them with an additional layer of security. When using two factor authentication, you’re required to enter a unique one time access code, along with your account password in order to be able to access the account. This code is sent to you by the service provider (over SMS or phone call), but it only works when you’re online and have the device to receive code. However, if you want the same code offline, you need an offline authenticator app, just like Google Authenticator.
I’m sure almost everyone of you have Google Accounts, and a fairly large number of you use 2FA to secure your accounts. Thus, the Google Authenticator app must be something that you use quite frequently, and are quite familiar with. But have you ever wondered, how does Google Authenticator (or any other similar app) actually work? How is it able to generate that unique one time access code that’s good for only 30 seconds? Keep reading, as we find out the answer, past the break.

What’s this all about?
Almost everyone of us are familiar with the Google Authenticator app, and we already know that this little app generates unique one time access codes, that must be entered along with the account password in order to gain access to our 2FA secured Google (and other services that Google Authenticator is compatible with) accounts. And as such, we’re not here to go over the app itself. Instead, we’ll be seeing how this app “actually” works, and how is it able to fire those unique codes offline, that your 2FA secured account instantly recognizes as valid, even though the two are not synchronized over any kind of active network.
The Time-based One-time Password algorithm and its mojo
Google Authenticator may be one of the most popular two factor authenticator apps out there, but it’s most certainly not the only one. In fact, Google Authenticator just uses an implementation of the wonderful Time-based One-time Password (TOTP) algorithm to generate unique codes. Other authenticator apps also use the implementation of TOTP to fire off unique codes offline. While the detailed working of TOTP is pretty abstruse, it basically involves computing a one time password (OTP) from a unique shared secret key and the current system time.
In order to compute the unique access codes, Time-based One-time Password algorithm combines both the shared secret key and current system timestamp with a cryptographic hash function. Check out the following flowchart, that gives a visual overview of how this is done:
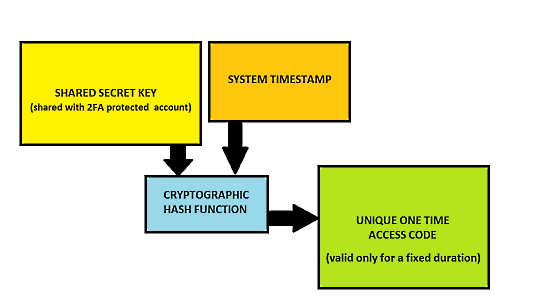
So how does Google Authenticator app work offline?
Now that we know the basics of the magical Time-based One-time Password (TOTP) algorithm that’s behind Google Authenticator (and other similar apps), it’s time to know how this whole system of your account and the authenticator app works together. The steps discussed below should clarify things:
Step 1: We start off things by setting up the online account (which can be anything from an email account to a cloud storage service) with the (Google) authenticator app after 2FA has been turned on for it. To add your account to Google authenticator, you’re either required to enter the account username with a special code, or scan the QR code generated by the service (for which 2FA is being configured). This QR code contains a unique shared secret key (mentioned in the previous section) that’s tied in to your account. Needless to say, no two accounts have the same shared secret key.
Step 2: Once the account has been successfully added to the authenticator app, the one-time setup is finished, and the app now has the unique shared secret key stored with its corresponding account info. From here on, every time you require a unique one-time access code, Google Authenticator will generate the same by combining this shared secret key and the current system timestamp with a special cryptographic hash function, effectively implementing Time-based One-time Password algorithm. The generated code is entered on the website’s code prompt:

Step 3: Now the question is, how does the website know that the code was generated for the same account? It’s simple, and this is where the current system timestamp comes into play. This timestamp increases in fixed intervals (e.g. 30 seconds), and the timestamps of both the code generating app and servers are roughly synchronized, at the time of setup.
This means that codes generated in that fixed duration of time for which they are valid would have more or less the same timestamp and definitely the same shared secret key. Consequently, the website where the code generated by the authenticator app is entered knows that the code has been generated by the authenticator app for a particular account, tied in with the shared secret key.
The fact that these codes are invalidated after 30 seconds provides some extra security as well. Since the timestamps are synchronized on both ends, an invalidated code whose 30 second window has expired won’t work on the 2FA secured account. That’s all there’s to it! Ain’t that hard, right?
Also See: What is Two Factor Authentication? Why You Should Care? [ILFS Explains]
Conclusion
Apps like Google Authenticator, and Two factor authentication in general, provide a much needed extra line of defense to our online accounts. On the surface, it might seem that those random numeric codes that change after 30 seconds don’t have much to them. However, I’m sure after reading this article, you’ll know (and appreciate) the work that goes under the hood to make your precious online accounts safe and secure!