Browser in the Box is an ultra secure sandboxed web browser that’s sure to please those extremely wary about their online privacy and security. Made by the German company Sirrix AG, Browser in the Box ensures that your web browsing is completely secure and free from any kind of online threats (malware, phishing attacks etc.). How it achieves this is also equally interesting: Browser in the Box runs a separate copy of the Firefox web browser in a completely sandboxed environment, and that too on a hardened version of Debian Linux acting as a virtual machine. Each browsing session is treated separately from the other, and is immediately terminated once the application is closed. To top it all off, Browser in the Box even includes a built-in standard certified boot image, that it gets reset to every time it’s restarted. Sounds like something that you can use to secure your online browsing activity? Head past the break to find out more.

A few words about the two major technologies used by Browser in the Box
There are two major computing technologies that work their mojo at the back-end of Browser in the Box to make sure that your entire web browsing experience stays secure and protected from prying eyes. Hence, a few words about these two are in order
Sandboxing:
Basically, a Sandbox is a container placed around an application running on Windows (or any other) Operating System. This means that anything created or modified (files, menu settings etc.) by the sandboxed application is not available to the Operating System that it’s running on. Even the changes made by the Sandboxed application are not saved once the application is terminated. However, the application itself has full access to anything in the Operating System that it would’ve been able to access, had it not been Sandboxed.
Virtual Machine:
In the simplest terms, a Virtual Machine can be considered as a superset of a Sandbox. But that’s where the similarities end. Contrary to Sandbox, which is just a container providing an encapsulated environment to an application to run on an installed Operating System, a Virtual Machine actually simulates an entire Operating System running inside the actual Operating System. Thus a Virtual Machine is actually a machine within a machine, that doesn’t exist in actuality, but rather mimics an actual computer or Operating System (hence the name, Virtual Machine).
Also See: Run programs in isolated space using Sandboxie
How these two technologies make Browser in the Box uber-secure?
Browser in the Box uses both Sandboxing and Virtual Machines to make each browsing session of yours completely secure and free from any kind of potential web-based threats. On the core level, it runs a stable version of Firefox (version 24.3.0, as per the current release) sandboxed inside its own isolated environment. However, that’s just the first half. This sandboxed copy of Firefox itself runs on a Linux-based Guest Operating System (Debian), running as a virtual machine (using Oracle VirtualBox) on your actual host Operating System. It’s due to this reason, that the installer for Browser in the Box also includes a copy of Oracle VirtualBox and Debian Linux as well. No wonder it’s about 470 MB in size.
This means that your entire interaction with Browser in the Box (or Firefox) is contained within its own sandboxed environment, and then within the Debian Guest Operating System, isolated from the actual OS. How cool is that?
But you know what’s the real kicker? Get this: Every time you restart Browser in the Box (or close it and run it again, which equates to the Virtual Machine powering off and then back on), it gets reset to a certified boot image. This means that even if malware and other bad things manage to get in during your browsing session, they won’t be there the next time Browser in the Box is run. It’s like restoring your entire OS to factory default settings every time it restarts. Now that, is awesome!
Also See: Wipeout private browser
Browser in the Box: Installation and Main UI
Although Browser in the Box is pretty complicated in itself, its installation is a pretty standard affair. All you have to do is download the hefty (almost 500 MB) installer for the freely available home version (The paid versions are meant for enterprises) from Sirrix’s homepage, and install it. The download and installation both can take a while, considering the download size as well as the extra application (Oracle VirtualBox) that’s installed. Once installed, execute Browser in the Box. Here’s how the user interface looks like:
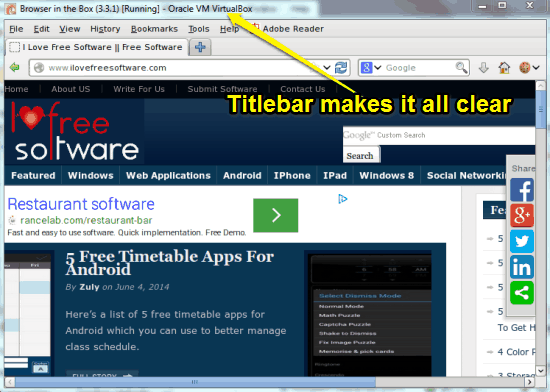
Looks familiar, right? Well it should, considering that’s just your good ol’ pal Mozilla Firefox. Visually, there are not many differences in the regular Firefox vs. the Browser in the Box turbocharged Firefox, except that it looks kind Linux-ish (And why it wouldn’t, it’s running inside Debian Linux, after all). However, check out the Titlebar text, that makes it all clear. It reads “Browser in the Box (3.3.1) Running – Oracle VM VirtualBox”. This means that your browsing is secure from even your host Operating System. Go ahead and have fun on the Internet.
Also see: Browser For Private Browsing That Deletes All Traces of Browsing History
Secure Sandboxed Web Browsing with Browser in the Box:
Web Browsing using Browser in the Box is super secure. Still, it is pretty regular and fun. I mean, from an end user’s perspective, there are not much differences. You can access websites regularly, view online videos, use your email, and pretty much anything that you can do on your normal browser. But the big difference is that all of this is secured, isolated from even your own Operating System.
However, Browser in the Box works differently when it comes to downloading and uploading stuff, since both of these activities require interaction with the Operating System. If you download anything (e.g. a song, a software application etc.) from Browser in the box, your downloads are automatically stored into a secure shared folder existing within the Debian Linux VM Operating System, and from there, they are securely transferred to the default download location in your host Operating System.
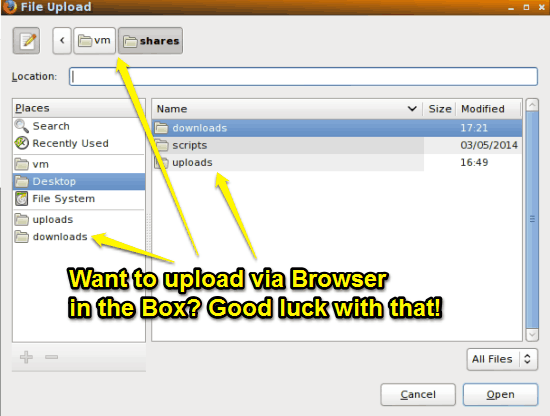
Similarly, if you want to upload something (say, to one of your cloud storage accounts) via the web UI using Browser in the Box, then you’re out of luck. That’s because when you try to browse to the location of the content that you want to upload, all you’ll get are the default system folders of the VM running Debian Linux, and obviously you can’t save anything in them, since the only reason that VM running Guest OS exists is to run Browser in the Box.
Conclusion
Browser in the Box is an amazing application that uses two extremely well-known security/virtualization technologies to provide you with possibly the safest web browsing experience ever. Granted, the need to install an extra application (Oracle VirtualBox), and the big download size, coupled with the inability to upload to your cloud accounts maybe a few downers, but this thing more than makes up for it by giving you ultra secure two layered protection from even your own host Operating System. If you take your online privacy seriously (correction: maybe a little bit too much seriously), this is just what you need.